Operational Technology (OT) refers to the hardware and software systems used to monitor and control physical processes in industries such as manufacturing, energy, transportation, and utilities. With the increasing interconnectivity of OT systems and their integration with enterprise IT networks, the need for robust cybersecurity measures becomes paramount. The Purdue Model of Cybersecurity provides a framework for understanding the complex layers of security required to protect OT environments. In this article, we will delve into the Purdue Model and explore its application to safeguarding OT systems.
Understanding the Purdue Model
The Purdue Model of Cybersecurity, also known as the Purdue Enterprise Reference Architecture (PERA), was developed in the 1990s by researchers at Purdue University. It provides a hierarchical framework that categorizes OT systems into distinct levels based on their functions, responsibilities, and levels of interaction with the physical processes they control. The model serves as a guide for implementing cybersecurity measures and segregating network traffic within OT environments.
The Purdue Model consists of six levels, each representing a specific component of the OT infrastructure:
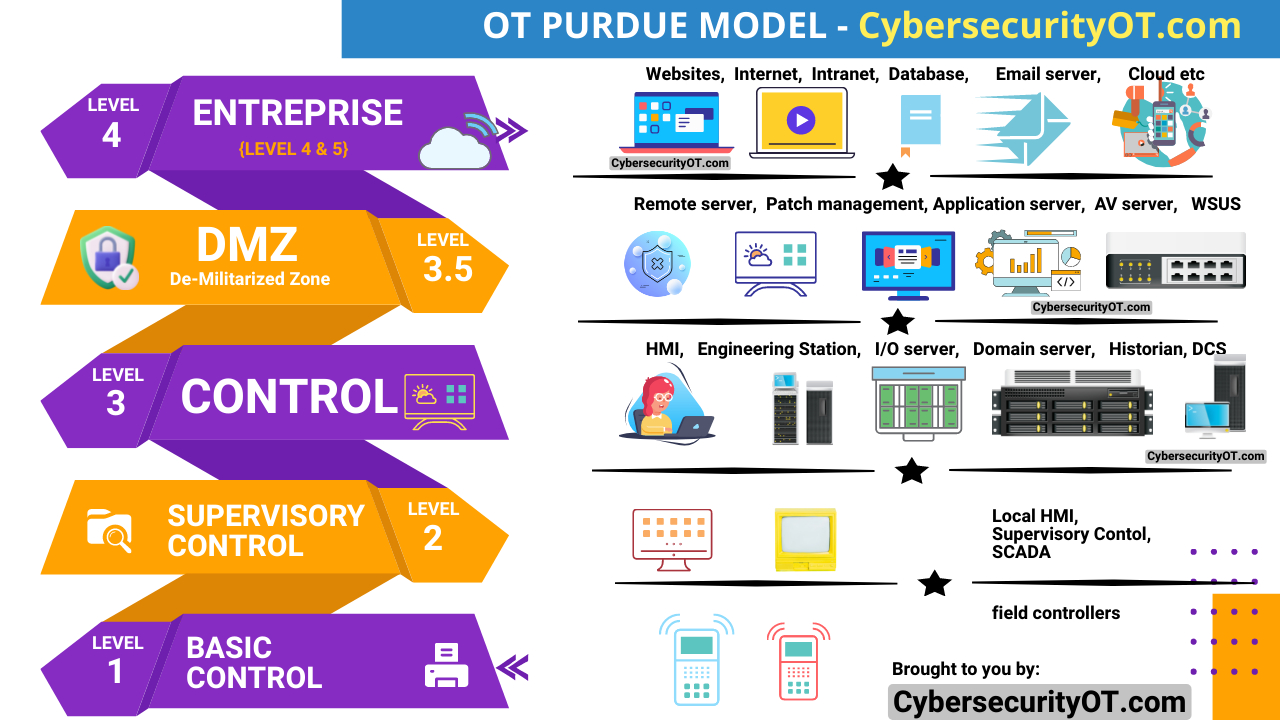
Level 0: Process (Note: Levels 0 & 1 are considered as level 1 In many cases)
At the lowest level, Level 0, the physical processes and equipment that form the core of OT systems reside. This includes devices such as sensors, actuators, motors, valves, and other industrial equipment responsible for controlling and monitoring physical operations. Level 0 is isolated from the network infrastructure to ensure the integrity and safety of the physical processes.
Since Level 0 deals with physical equipment and processes, the focus is on ensuring the safety and integrity of industrial devices. Measures such as physical security, access controls, safety systems, and protection against physical tampering are crucial. In some cases, air-gapping, which isolates Level 0 from the rest of the network, may be employed to reduce the attack surface.
Level 1: Basic Control (Note: Levels 0 & 1 are considered as level 1 In many cases)
Level 1 is where basic control functions take place. Level 1 comprises systems and assets that monitor and send commands to the devices at Level 0. Examples include Programmable Logic Controllers (PLCs), Remote Terminal Units (RTUs), and Intelligent Electronic devices (IEDs). The communication within Level 1 is typically limited to the immediate control functions and is isolated from higher-level systems.
Level 2: Supervisory Control
Level 2, also known as the supervisory control level, involves supervisory control and data acquisition (SCADA) systems. SCADA systems gather data from Level 1 controllers and provide operators with a centralized view of the processes. They enable monitoring, data logging, visualization, and basic control functions. Level 2 systems communicate with Level 1 controllers and may exchange limited data with Level 3 systems for reporting and monitoring purposes.
SCADA systems at Level 2 are often the primary target for cyberattacks due to their central role in controlling and monitoring industrial processes. Key cybersecurity measures include strong authentication and authorization mechanisms, secure remote access controls, encrypted communication channels, intrusion detection and prevention systems, and robust incident response capabilities.
Level 3: Control Center / Manufacturing Operations
Level 3 focuses on the manufacturing operations management (MOM) layer. This is also known as the control center. It includes functions such as production scheduling, inventory management, quality control, and performance monitoring. Level 3 systems, often referred to as manufacturing execution systems (MES), gather data from SCADA systems and provide higher-level coordination and decision-making capabilities. The communication at this level is predominantly one-way, with limited interaction with the lower levels.
At Level 3, the focus shifts to protecting MES systems and their interactions with the lower levels. Security measures include access controls, network segregation, encryption of sensitive data, secure data exchange protocols, backup and recovery mechanisms, and continuous monitoring for anomalies and potential security breaches.
Level 3.5: DMZ (De-Militarized Zone)
In the Purdue Model of Cybersecurity, a Demilitarized Zone (DMZ) plays a crucial role in providing an additional layer of security and network segmentation. It acts as a buffer zone between the external network (e.g., the internet) and the internal OT network, protecting critical OT systems from direct exposure to potential threats. The DMZ serves as a controlled environment for hosting public-facing services and allows for secure communication with external entities while minimizing the risk of unauthorized access to sensitive OT assets.
The architecture requirements of a DMZ in the Purdue Model are as follows:
- Physical or Logical Separation: The DMZ should be physically or logically separated from both the external network and the internal OT network. Physical separation involves the use of separate network segments, while logical separation can be achieved through virtual LANs (VLANs) or virtualization technologies.
- Multiple Zones: The DMZ typically consists of multiple zones based on the specific security requirements of the services hosted within it. These zones include:a) External Zone: This zone is exposed to the external network, such as the internet. It contains security measures like firewalls, intrusion detection systems (IDS), and intrusion prevention systems (IPS) to monitor and filter incoming traffic.b) Perimeter Zone: Also known as the “DMZ proper,” this zone hosts publicly accessible services, such as web servers, email servers, or VPN gateways. It acts as a buffer between the external network and the internal OT network.c) Internal Zone: This zone is adjacent to the internal OT network and contains additional security measures to protect the critical OT assets from unauthorized access. It may include firewalls, access control mechanisms, and security monitoring systems.
- Access Control Mechanisms: The DMZ architecture requires strict access control mechanisms to regulate communication between the different zones. Access control lists (ACLs), firewalls, and network segmentation are implemented to allow authorized traffic and prevent unauthorized access to sensitive OT systems.
- Intrusion Detection and Prevention Systems: Intrusion detection and prevention systems are deployed within the DMZ to monitor network traffic, identify potential security threats, and take appropriate action to prevent unauthorized access or malicious activities.
- Encryption and Secure Communication: Secure communication protocols, such as Transport Layer Security (TLS) or Secure Shell (SSH), should be used to protect data transmitted between the DMZ and external entities.
- Logging and Monitoring: Robust logging and monitoring mechanisms should be implemented within the DMZ to capture and analyze network traffic, detect potential security incidents, and support forensic investigations.
- Redundancy and High Availability: The DMZ should be designed with redundancy and high availability in mind to ensure the continuous operation of critical services hosted within it. This may involve the use of load balancers, redundant servers, and failover mechanisms.
- Regular Updates and Patching: All devices and software within the DMZ should be regularly updated with the latest security patches to address known vulnerabilities and protect against emerging threats.
By incorporating a DMZ into the Purdue Model, organizations can establish a secure and controlled environment for hosting public-facing services, while protecting critical OT assets from direct exposure to external threats. It helps mitigate the risks associated with external connections and enhances the overall security posture of the OT infrastructure.
Level 4: Business Planning (Note: Levels 4 & 5 are considered as level 4 In many cases)
Level 4 represents the business planning and logistics layer. It encompasses enterprise resource planning (ERP) systems, supply chain management (SCM) systems, and other business-level applications. Level 4 systems gather data from Level 3 and provide business intelligence, forecasting, and resource planning capabilities. The communication at this level is primarily concerned with data reporting and analysis.
Level 4 systems, being more connected to enterprise IT networks, require robust security measures to protect sensitive business data and prevent unauthorized access. Measures include secure network architecture, encryption of data in transit and at rest, intrusion detection and prevention systems, security information and event management (SIEM) systems, and regular security assessments.
Level 5: Enterprise IT (Note: Levels 4 & 5 are considered as level 4 In many cases)
The highest level, Level 5, pertains to the enterprise IT network. It encompasses corporate-level systems, such as email servers, file servers, databases, and other IT infrastructure components. Level 5 systems provide services and support for the entire organization but have limited direct interaction with the lower levels of the OT infrastructure.
Enterprise IT networks at Level 5 need comprehensive cybersecurity measures to protect against a wide range of threats. This includes network segmentation, firewall protection, secure remote access controls, vulnerability management, security awareness training, regular patching and updates, and incident response capabilities.
Challenges and Best Practices w.r.t Purdue Model
Implementing the Purdue Model of Cybersecurity in OT environments comes with several challenges:
- Legacy Systems: Many OT systems rely on legacy equipment and protocols that may not have built-in security features. Retrofitting security controls and updating outdated systems can be challenging.
- Integration Complexity: The integration of OT and IT systems requires careful planning and coordination to ensure secure and seamless communication between the different levels.
- Skills Gap: OT cybersecurity requires specialized knowledge and skills that may be lacking in many organizations. Training and developing a skilled workforce is essential.
- Continuity of Operations: Implementing security controls should not compromise the availability and reliability of critical OT systems. Ensuring business continuity is vital.
To address these challenges, organizations should adopt the following best practices:
- Risk Assessment: Conduct regular risk assessments to identify vulnerabilities, prioritize security controls, and allocate resources effectively.
- Defense-in-Depth: Implement a layered security approach that includes technical, procedural, and physical controls at each level of the Purdue Model.
- Network Segmentation: Segregate OT networks into zones and implement firewalls and access controls to control the flow of network traffic between the different levels.
- Vendor Management: Engage with vendors to ensure the security of OT systems, including regular patching, updates, and adherence to cybersecurity best practices.
- Incident Response: Develop an effective incident response plan tailored for OT environments, including incident detection, containment, eradication