Introduction:
With the increasing digitization and interconnectedness of industrial automation and control systems (IACS), it has become imperative to establish robust cybersecurity measures to protect these critical infrastructures. The International Electrotechnical Commission (IEC) developed the IEC 62443 standard series, which provides a comprehensive framework for securing IACS throughout their lifecycle. This essay delves into the crucial process of establishing an IACS security program as per the guidelines outlined in IEC 62443. By understanding the key steps and components of this program, organizations can enhance their cybersecurity posture, mitigate risks, and safeguard the integrity, availability, and confidentiality of their industrial control systems.
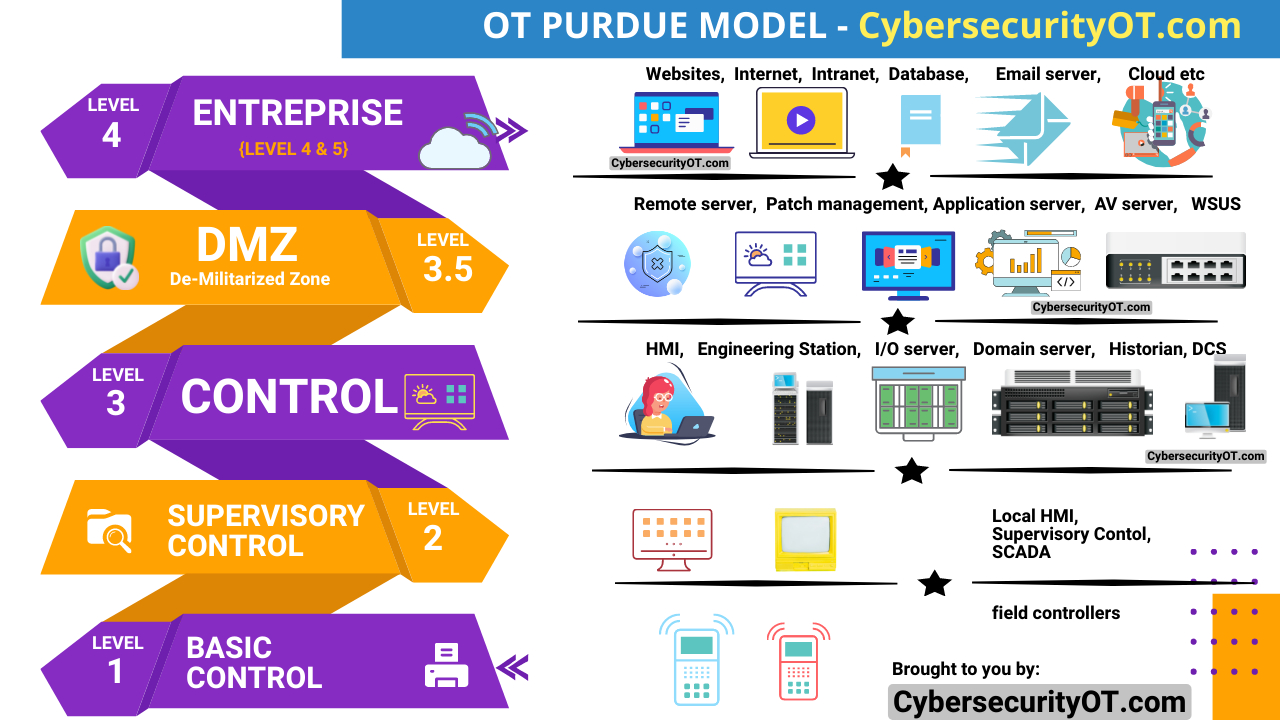
IEC 62443 2-1 is the core document which defines and explains how to establish IACS program.

Understanding the IACS Security Program:
The IACS security program provides a structured approach to identify, assess, and address cybersecurity risks within an industrial control system environment. It encompasses a range of activities, policies, procedures, and technical measures aimed at preventing, detecting, responding to, and recovering from cyber incidents. The program considers the unique characteristics and requirements of IACS, including the operational technology (OT) environment, equipment lifetime, and specific performance and availability needs.
Key Components of an IACS Security Program:
a) Leadership and Governance:
A successful IACS security program begins with strong leadership and governance. It involves establishing clear roles, responsibilities, and accountability for cybersecurity, both at the organizational level and within the IACS team. This component ensures that cybersecurity is prioritized, integrated into business processes, and aligned with the organization’s overall risk management strategy.
b) Risk Assessment:
Conducting a comprehensive risk assessment is essential to identify potential vulnerabilities, threats, and impacts within the IACS environment. The assessment should consider both technical and non-technical aspects, such as physical security, human factors, and supply chain risks. By understanding the specific risks, organizations can prioritize their efforts and allocate resources effectively.
c) Security Policies and Procedures:
Developing and implementing robust security policies and procedures is vital to establish a strong security culture. These policies outline expectations, standards, and guidelines for secure practices within the organization. They cover areas such as access control, incident response, data protection, configuration management, and employee awareness training. Regular reviews and updates ensure that policies remain relevant and effective.
d) Security Controls and Countermeasures:
Implementing appropriate security controls and countermeasures is a critical aspect of an IACS security program. This includes technical measures such as network segmentation, intrusion detection systems, encryption, authentication mechanisms, and secure remote access. Physical security controls, such as video surveillance, access controls, and environmental monitoring, are also essential to protect IACS assets.
e) Monitoring and Incident Response:
Continuous monitoring of IACS networks, systems, and devices is crucial to detect and respond to security incidents promptly. Monitoring tools and techniques, including log analysis, security information and event management (SIEM) systems, and real-time alerts, enable organizations to identify anomalous behavior, indicators of compromise, and potential threats. An effective incident response plan should be in place to address incidents rapidly and minimize their impact.
f) Training and Awareness:
Human factors play a significant role in IACS security. Providing regular training and awareness programs helps equip employees with the knowledge and skills necessary to identify and respond to security threats. Training should cover topics such as social engineering awareness, password hygiene, secure system configurations, and incident reporting procedures.
Implementing an IACS Security Program:
a) Establishing a Cross-functional Team:
Building a dedicated team comprising representatives from various departments, including IT, OT, security, operations, and management, is crucial to successfully implementing an IACS security program. This team should collaborate to define goals, develop policies and procedures, and drive the implementation process.
b) Security Program Implementation:
The implementation phase involves executing the activities defined in the program, including risk mitigation, control implementation, and monitoring. Organizations should follow the guidance provided by IEC 62443, aligning their efforts with the relevant standards, technical reports, and technical specifications.
c) Documentation and Communication:
Documenting the IACS security program, including policies, procedures, and technical configurations, ensures that the organization has a clear reference for future actions and compliance requirements. Additionally, effective communication of the program across the organization helps foster awareness, understanding, and compliance.
d) Continuous Improvement:
An IACS security program is not a one-time endeavor but an ongoing process. Organizations should regularly review and assess the effectiveness of their security controls, identify areas for improvement, and adapt their program to emerging threats and technological advancements. Feedback from incident response, audits, and risk assessments should inform these continuous improvement efforts.
Conclusion:
Establishing an IACS security program as per the guidelines of IEC 62443 is critical for organizations relying on industrial automation and control systems. By implementing a comprehensive program encompassing leadership and governance, risk assessment, security policies and procedures, security controls, monitoring and incident response, and training and awareness, organizations can significantly enhance their cybersecurity posture.
This proactive approach to securing IACS throughout their lifecycle helps mitigate risks, protect critical assets, ensure operational continuity, and safeguard against potentially devastating cyber threats. Adhering to the principles and best practices outlined in IEC 62443 enables organizations to stay ahead of evolving cybersecurity challenges and maintain the integrity, availability, and confidentiality of their industrial control systems.