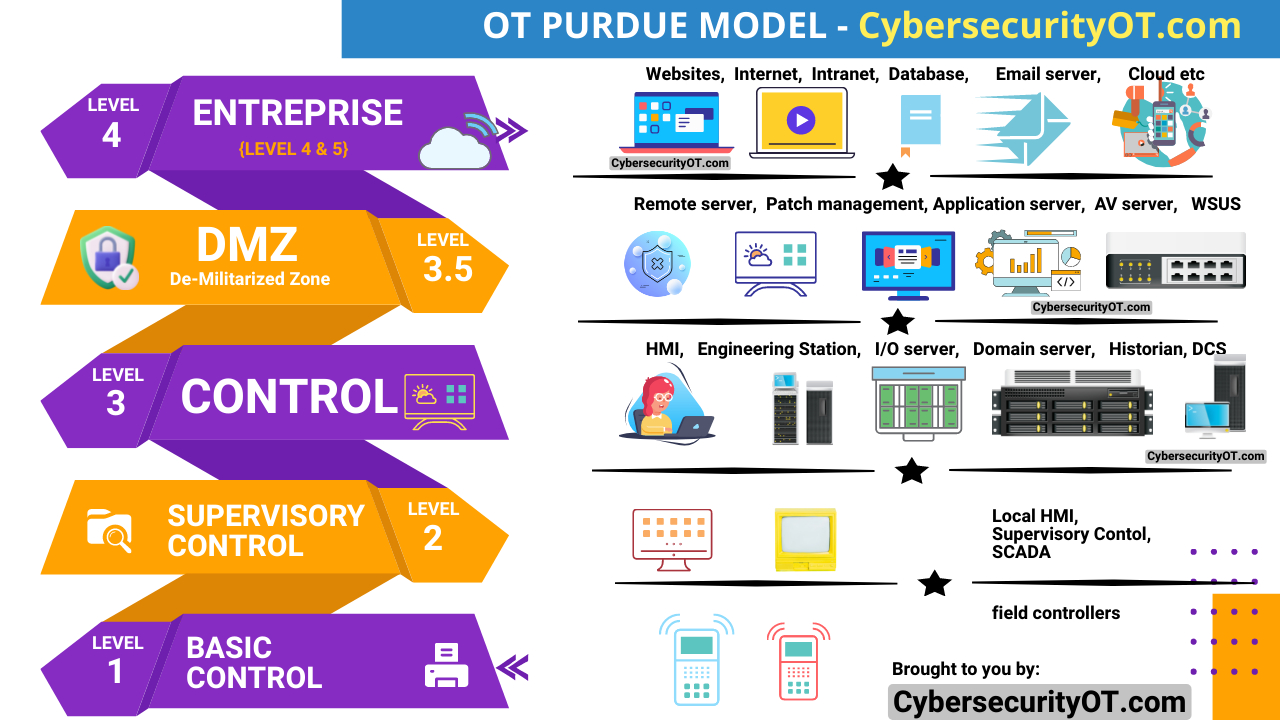
The seven foundational requirements (FRs) of IEC 62443 are:
- Identification and authentication control (FR1)
- Use control (FR2)
- System integrity (FR3)
- Data confidentiality (FR4)
- Restricted data flow (FR5)
- Timely response to events (FR6)
- Resource availability (FR7)
These requirements are designed to help organizations protect their industrial automation and control systems (IACS) from cyberattacks.
FR1: Identification and authentication control
FR1 requires organizations to reliably identify and authenticate all users (humans, software processes, and devices) attempting to access the IACS. This can be done through a variety of methods, such as passwords, biometrics, and two-factor authentication.
FR2: Use control
FR2 requires organizations to enforce the assigned privileges of an authenticated user (human, software process, or device) to perform the requested action on the system or assets. This can be done by using role-based access control (RBAC) to define which users have access to which resources and what actions they are allowed to perform.
FR3: System integrity
FR3 requires organizations to ensure the integrity of the IACS to prevent unauthorized manipulation. This can be done by implementing a variety of security controls, such as:
- Secure coding practices
- Configuration management
- Change management
- Patch management
- Security testing
FR4: Data confidentiality
FR4 requires organizations to ensure the confidentiality of information on communication channels and in data repositories. This can be done by using a variety of security controls, such as:
- Data encryption
- Access control
- Data masking
- Data loss prevention
FR5: Restricted data flow
FR5 requires organizations to segment the IACS via zones and conduits to limit the unnecessary flow data. This can be done by using a variety of security controls, such as:
- Firewalls
- IDS/IPS
- Network segmentation
- Data flow analysis
FR6: Timely response to events
FR6 requires organizations to have the necessary capabilities to respond to security violations by notifying the proper authority, reporting evidence of the violation, and taking timely corrective action upon discovery of such an incident. This can be done by implementing a variety of security controls, such as:
- Security incident response plan
- Security awareness training
- Security monitoring
- Security auditing
FR7: Resource availability
FR7 requires organizations to ensure that the design and operation of the IACS is such that there are no “denial or service” situations, where the IACS is unavailable to authorized users. This can be done by implementing a variety of security controls, such as:
- Disaster recovery plan
- Business continuity plan
- Redundancy
- Load balancing
By implementing these seven foundational requirements, organizations can significantly improve the security of their IACS.