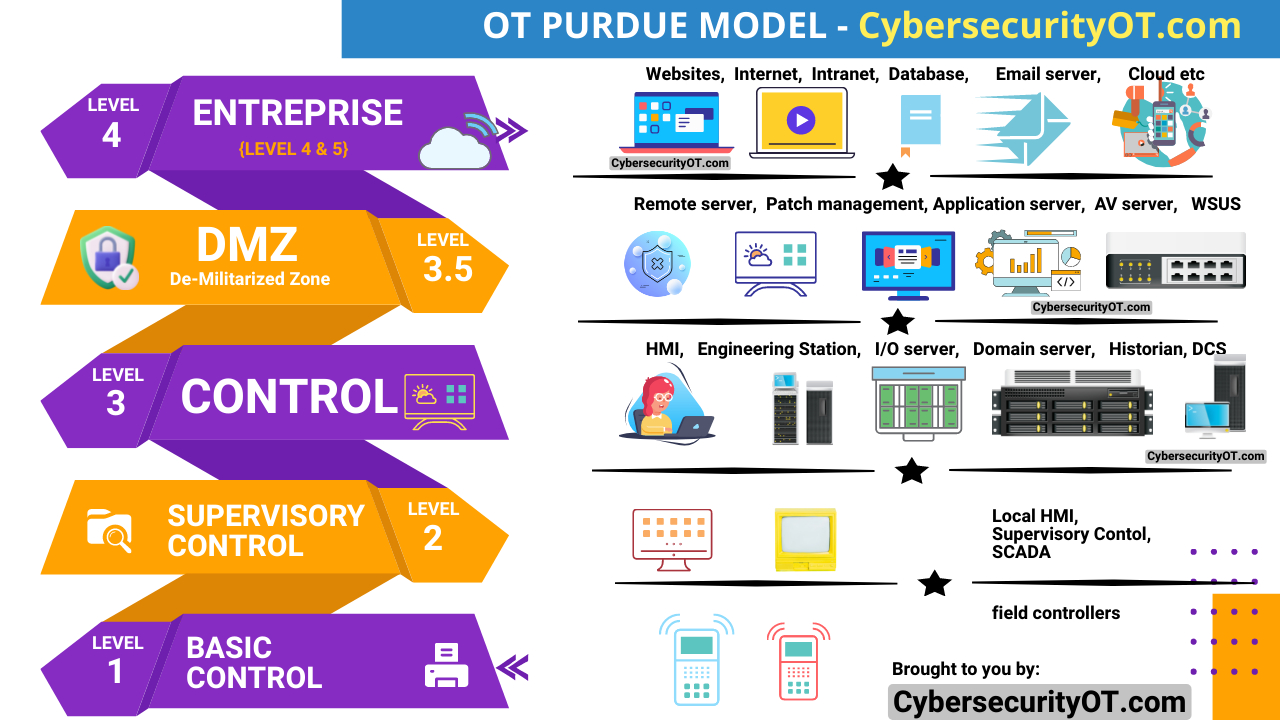
The Kingdom of Saudi Arabia, a global leader in the oil and gas industry, takes cybersecurity seriously. To address the evolving cyber threat landscape and protect its critical infrastructure, the National Cybersecurity Authority (NCA) implemented the Operational Technology Cybersecurity Controls (OTCC) in 2022.
What is OTCC?
The OTCC is a comprehensive cybersecurity controls framework that outlines mandatory controls for organizations operating Industrial Control Systems (ICS) or OT in Saudi Arabia. Due to increased attacks in the critical infrastructure & manufacturing in general, it was need of the hour to come up with mandate for companies to secure their assets. OTCC was created on similar lines as ECC (Essential Cybersecurity Controls, read more on ECC below) & are extension to ECC aimed at OT/ICS environments. OTCC is a mandate.
ICS are computer systems that control and monitor essential industrial processes, making them prime targets for cyberattacks.
Why is OTCC Important?
The OTCC is crucial for several reasons:
- Enhanced Security: It establishes a baseline for robust cybersecurity practices, safeguarding critical infrastructure from cyber threats.
- National Security: By protecting ICS, OTCC helps ensure the smooth operation of critical sectors like oil and gas, power generation, and water treatment facilities.
- Compliance: Organizations that adhere to OTCC demonstrate their commitment to cybersecurity best practices, potentially reducing insurance costs and attracting new business partnerships.
Understanding OTCC
OTCC Structure
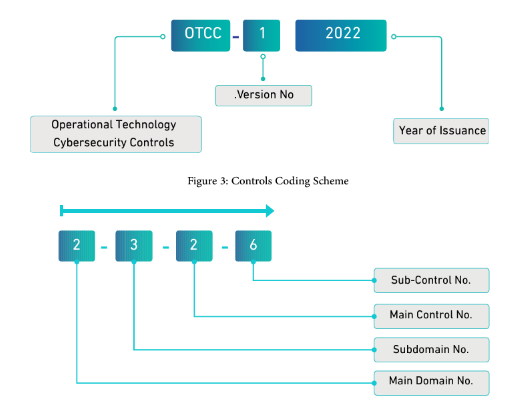
OTCC controls have been segregated in the following:
- 4 Main Domains.
- 23 Subdomains.
- 47 Main Controls.
- 122 Subcontrols.
OTCC Levels
One of the most interesting things about OTCC is the levels. It highlights the research done for making the controls. Not every unit is required to implement the best security controls. There are different types of OT units, small & large. It is difficult for smaller units to comply to many of the ICS/OT cybersecurity requirements or standards. Investing large amount on cybersecurity for small or older OT environments may not be feasible, or economical.
Hence OTCC came out with a “Facility Identification Tool”. Using the tool, asset owners and/or their consultants can identify the criticality of a particular OT/ICS facility. Outcome of this will be one of the 3 levels as mentioned below:

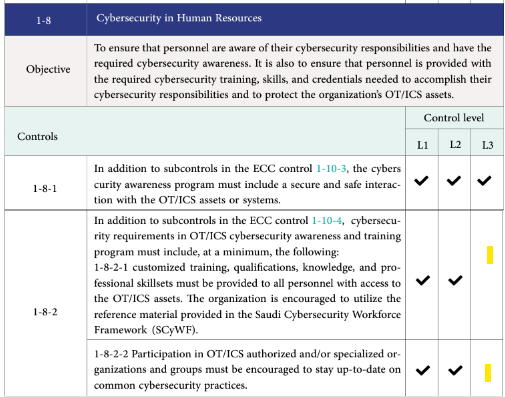
Evidently, if a facility has lower criticality ranking, it has lesser controls to comply to. For example, in the image below, facility identified as L3 is not required to comply to 1-8-2 (Please note that this is unchecked).
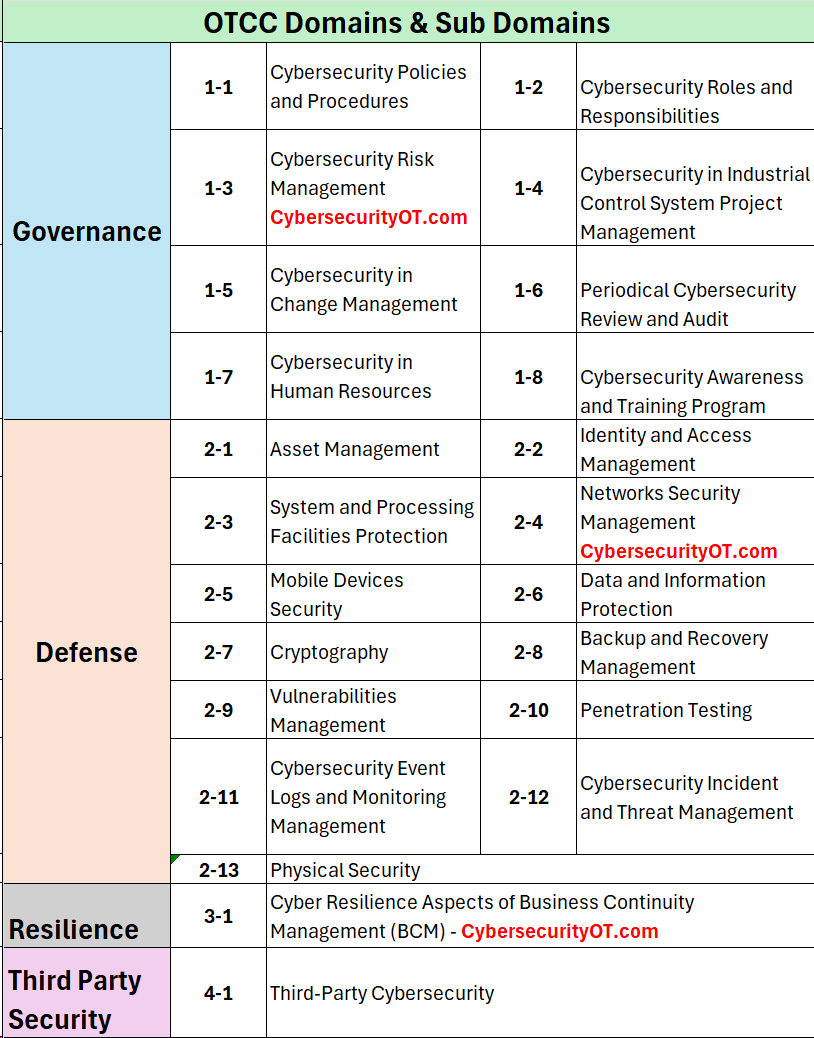
OTCC Domains & Sub Domains:
Each sub domain is followed by control & sub control. The below image is captured from the OTCC document:
OTCC: Aligning with Global Standards
The OTCC incorporates best practices and international cybersecurity standards, ensuring it remains relevant and effective in the global fight against cybercrime. OTCC utilized the following international standards:
- IEC 62443
- NIST 800-82
- NIST 800-53 CSF
- NOG 104 (Norway)
- NERC CIP
- DoE’s C2M2 model.
What is ECC?
ECC or “Essential Cybersecurity Controls” is indeed a framework or standard used in Saudi Arabia, it include a set of essential security controls that organizations within the country are expected to implement to protect against common cyber threats and vulnerabilities. These controls could be based on international best practices and standards such as the NIST Cybersecurity Framework, ISO/IEC 27001, or other relevant standards. It has a total of 5 Key domains one of which is ICS security.
What is the relation between ECC & OTCC?
One key question comes to mind by many professionals & leaders is the relation between ECC & OTCC. There is already a domain on ICS security in ECC. So what is the need for OTCC?
The answer is simple: OTCC can be considered as an extension to ECC. First, OTCC is focused purely on the OT/ICS controls. Second, it should be noted that there are many references to ECC within the OTCC.
For example, the below image taken from sub domain 1-6 of OTCC which is about periodic cybersecurity review & audit. I have highlighted text in the main control 1-6-1. It says, “with reference to ECC control 1-8-1 ….”. This clearly means while performing OTCC audit or implementation, one need to refer to ECC standard also.

What’s Next for OTCC?
The OTCC is a significant step towards a more secure digital landscape in Saudi Arabia. As cyber threats continue to evolve, we can expect the NCA to refine and update the OTCC to stay ahead of the curve. The current version “:2022” came in 2022 & is quite comprehensive. There will be future updates coming for OTCC in the coming days. With Saudi Arabia working on its mission 2030, it is leaving no stone unturned to protect its critical infrastructure.