Introduction:
In today’s interconnected digital landscape, organizations face an increasing number of sophisticated cyber threats. To safeguard critical assets and data, a proactive and comprehensive approach to cybersecurity is essential. One such approach is defense in depth, which involves deploying multiple layers of security controls to provide overlapping protection and minimize the potential impact of cyber-attacks. This article explores the concept of defense in depth, its core principles, and its significance in enhancing cybersecurity resilience.
Understanding Defense in Depth:
Defense in depth, also known as layered security, is a strategy that aims to create multiple lines of defense to protect against a wide range of cyber threats. Rather than relying solely on a single security measure, defense in depth employs a combination of preventive, detective, and corrective controls at different layers of an organization’s IT infrastructure. These layers can include physical, network, host, application, and data security.
Core Principles of Defense in Depth
a) Principle 1 – Layered Approach:
Defense in depth involves implementing multiple layers of security controls. Each layer adds an additional level of protection, making it more challenging for attackers to compromise the system. Examples of security layers include firewalls, intrusion detection systems, antivirus software, and secure coding practices.
b) Principle 2 – Diversity of Controls:
Defense in depth encourages the use of diverse security controls to address various attack vectors. By employing a mix of technical, procedural, and physical controls, organizations can mitigate risks effectively. This diversity prevents the exploitation of a single vulnerability that may exist in a particular control.
c) Principle 3 – Redundancy and Resilience:
Defense in depth incorporates redundancy to ensure that if one security measure fails, there are backups in place to maintain system integrity. Redundancy minimizes single points of failure and enhances system resilience, allowing organizations to continue operations even during cyber-attacks or system disruptions.
d) Principle 4: Defense Across the Attack Lifecycle:
Defense in depth considers the entire attack lifecycle, from pre-breach to post-breach stages. It focuses not only on preventing initial compromises but also on detecting, containing, and recovering from security incidents. This comprehensive approach improves incident response capabilities and reduces the time to detect and mitigate attacks.
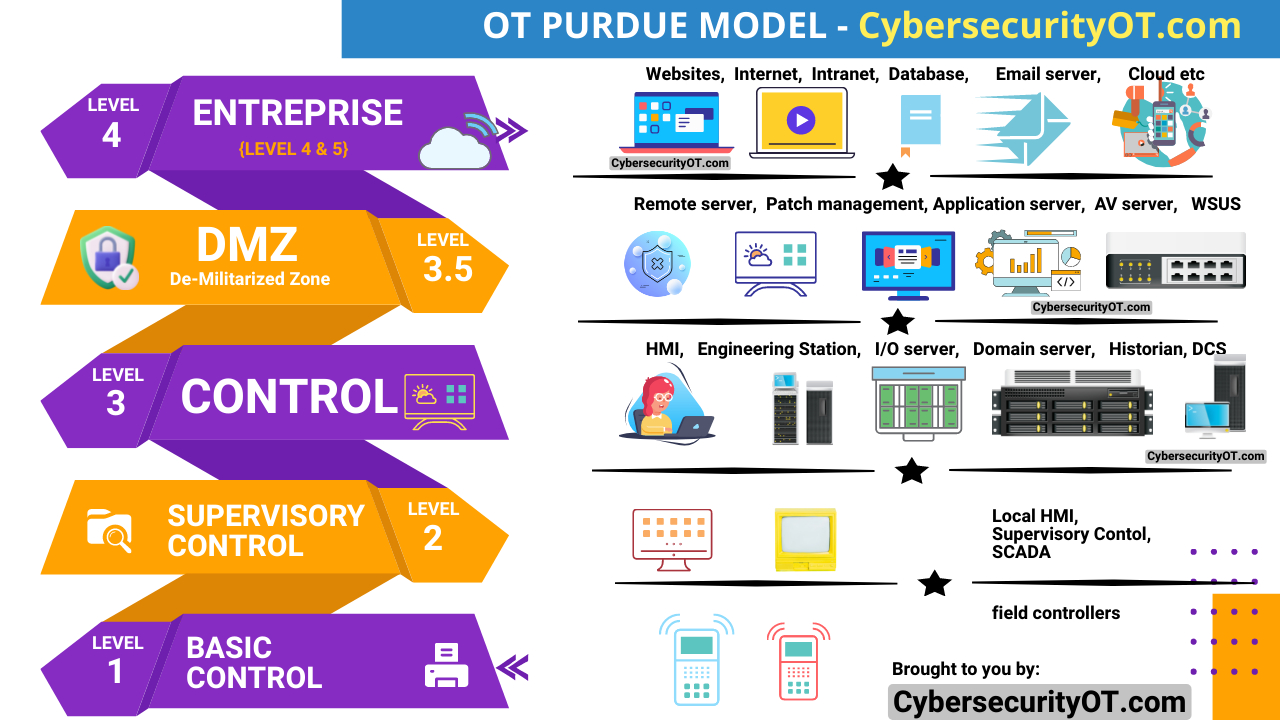
Layers of Defense in Depth:
a) Physical Security:
The first layer of defense involves securing physical access to infrastructure components, such as data centers, servers, and networking equipment. Measures may include surveillance systems, access controls, and physical barriers to prevent unauthorized entry.
b) Perimeter Security:
The perimeter layer establishes a boundary between the internal network and external threats. Firewalls, intrusion prevention systems (IPS), and virtual private networks (VPNs) are commonly used to monitor and filter incoming and outgoing network traffic.
c) Network Security:
Network security focuses on securing the internal network infrastructure. It involves measures such as network segmentation, network monitoring tools, access controls, and secure wireless networks to prevent unauthorized access and monitor network activity.
d) Host Security:
Host-based security aims to protect individual endpoints, including servers, workstations, and mobile devices. It involves implementing antivirus software, host intrusion detection systems (HIDS), and regular patch management to address vulnerabilities and detect potential compromises.
e) Application Security:
Application-layer security focuses on securing software applications and their associated components. Secure coding practices, application firewalls, and vulnerability scanning are crucial to prevent application-level attacks such as cross-site scripting (XSS) and SQL injection.
f) Data Security:
Data security involves protecting sensitive information throughout its lifecycle. Encryption, data loss prevention (DLP) techniques, access controls, and secure backup and recovery processes play vital roles in safeguarding data from unauthorized access, loss, or alteration.
g) User Education and Awareness:
The human factor is a critical component of defense in depth. User education and awareness programs provide training on best security practices, phishing awareness, social engineering techniques, and password hygiene. This layer helps employees become the first line of defense against cyber threats.
Implementing Defense in Depth:
Defense in depth is a key philosophy in securing the overall cybersecurity program. This approach is also in sync with the international standard IEC 62443.
a) Risk Assessment:
A comprehensive risk assessment helps identify potential vulnerabilities, threats, and impacts. It forms the foundation for designing an effective defense in-depth strategy tailored to an organization’s specific risks and requirements.
b) Layer Selection and Design:
Organizations should carefully select and design security layers based on their risk assessment results. Each layer should be complementary, providing a unique set of security controls that collectively strengthen the overall security posture.
c) Integration and Coordination:
To maximize the effectiveness of defense in depth, it is crucial to ensure seamless integration and coordination among the various security layers. This includes centralized logging and monitoring, sharing threat intelligence, and implementing incident response processes.
d) Regular Testing and Evaluation:
Continuous testing and evaluation of the defense-in-depth strategy are essential to identify weaknesses, vulnerabilities, and gaps in the security controls. Regular penetration testing, vulnerability assessments, and security audits help validate the effectiveness of each layer.
Conclusion:
Defense in depth is a comprehensive cybersecurity strategy that helps organizations mitigate the evolving threat landscape. By implementing multiple layers of security controls across physical, network, host, application, and data domains, organizations can significantly enhance their resilience to cyber-attacks.
The core principles of defense in depth, including layered approach, diversity of controls, redundancy, and resilience, and defense across the attack lifecycle, provide a robust framework for safeguarding critical assets.
However, it is important to note that defense in depth is not a one-time implementation but an ongoing process that requires regular assessment, testing, and adaptation to address emerging threats. With an effective defense in-depth strategy in place, organizations can better protect their systems, data, and reputation, ensuring a more secure digital environment.