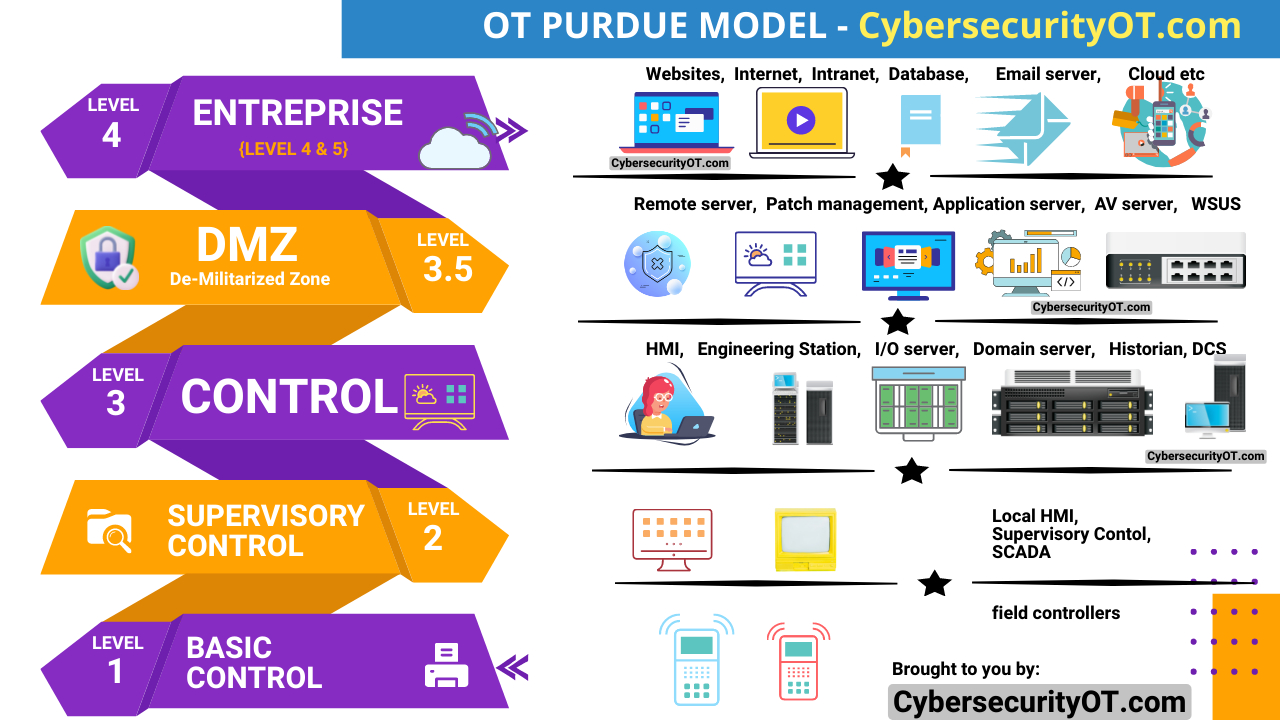
In cybersecurity, the concepts of zones and conduits are used to establish boundaries and define the flow of network traffic within an organization’s infrastructure. Zones represent logical or physical segments of a network with distinct security requirements, while conduits are the paths or connections between these zones. By properly identifying and securing zones and conduits, organizations can implement effective security measures and control the movement of data and information within their networks.
Let’s explore the best practices for identifying zones and conduits, along with examples from cybersecurity frameworks such as IEC 62443 and the NIST Cybersecurity Framework, as well as networking architecture.
Zones:
Zones can be defined based on the sensitivity and criticality of the assets and systems within a network. Here are some best practices for identifying zones:
- Asset Classification: Identify and categorize assets based on their importance, criticality, and the level of protection required. This helps determine the boundaries of different zones.
- Data Classification: Classify data based on its sensitivity, confidentiality, integrity, and availability requirements. This aids in establishing appropriate zones to protect sensitive information.
- Functional Boundaries: Define zones based on functional boundaries, such as separating user-facing systems from critical infrastructure, separating development and testing environments from production systems, and segregating administrative systems from operational systems.
- Risk Assessment: Conduct a thorough risk assessment to identify potential threats, vulnerabilities, and risks associated with different assets and systems. Use the findings to define zones that mitigate and address specific risks.
- Compliance Requirements: Consider regulatory and compliance requirements specific to your industry or organization when defining zones. These requirements may influence the need for segregated zones to protect sensitive data or meet specific security standards.
- Security Controls: Identify the security controls needed to protect assets within each zone. This includes firewalls, intrusion detection systems, access controls, encryption, and monitoring mechanisms.
Examples:
- In the IEC 62443 cybersecurity standard, zones are defined based on the level of protection required for critical infrastructure. For example, Zone 0 represents the most critical zone where immediate process control occurs, while Zone 4 represents less critical zones where administrative and business systems reside.
- The NIST Cybersecurity Framework identifies zones based on the criticality of systems and the protection levels required. For example, the framework recommends segregating the enterprise network from the OT network to control and monitor traffic between them.
- In networking architecture, zones can be established using techniques such as VLANs (Virtual Local Area Networks), where different VLANs represent separate zones with specific security policies and controls.
Conduits:
Conduits represent the connections or paths that allow data flow between zones. Best practices for identifying conduits include:
- Data Flow Mapping: Map the flow of data and information within the network to identify the connections between different zones. This helps understand the dependencies and potential risks associated with data movement.
- Network Topology Analysis: Analyze the network topology to identify physical and logical connections between zones. This includes identifying routers, switches, gateways, and other network devices that facilitate data transfer.
- Access Points: Identify access points or gateways that connect different zones and define the security controls and policies governing the flow of data through these access points.
- Third-Party Connections: Identify any third-party connections or connections to external networks (e.g., the internet) and establish secure conduits for data exchange while enforcing appropriate security measures.
- Data Validation and Filtering: Implement data validation and filtering mechanisms at conduits to prevent unauthorized or malicious data from entering critical zones.
Examples:
- In the IEC 62443 standard, conduits are defined as the connections between different zones. For example, Level 1 to Level 2 conduits represent the connections between basic control systems and supervisory control systems in an industrial control network.
- In the NIST Cybersecurity Framework, conduits are represented by connections between different security zones. For example, a secure VPN connection between the enterprise network and an external partner network represents a conduit that allows controlled data exchange.
- In networking architecture, conduits can be established using technologies such as firewalls, routers, and access control lists (ACLs) to control and monitor traffic between different zones.
By effectively identifying and securing zones and conduits, organizations can implement a strong network architecture that enhances security, mitigates risks, and ensures the confidentiality, integrity, and availability of critical assets and data.