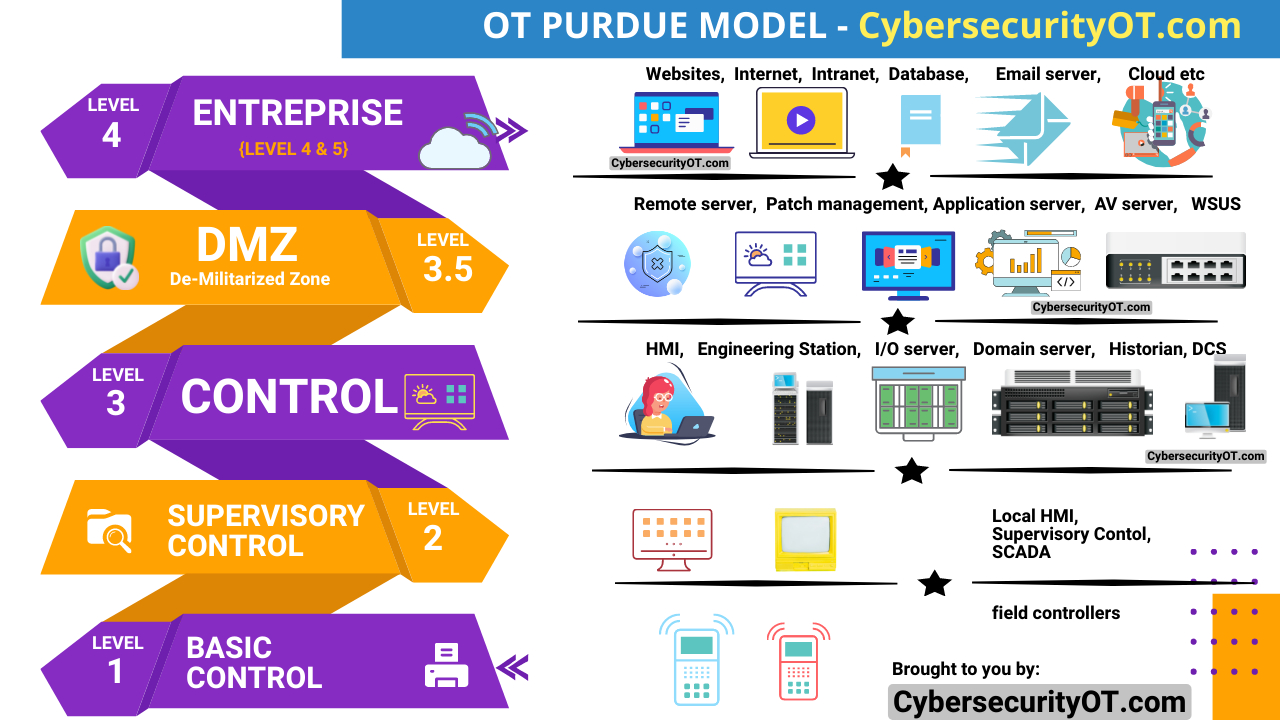
In recent years, the industrial landscape has witnessed a surge in cyber attacks targeting critical infrastructure and operational technology (OT) systems. These incidents pose a significant threat to the reliability, safety, and functionality of essential services. In this deep-dive analysis, we will explore some of the most notable recent industrial cyber attacks, examining their dates, causes, and mitigation strategies.
1. The Triton/Trisis Incident (2017):
Date: The Triton incident, also known as Trisis, occurred in 2017.
Cause: This attack targeted a petrochemical plant’s safety instrumented system (SIS) and was designed to manipulate the plant’s emergency shutdown capabilities. The malware, Triton, was specifically crafted to disable or manipulate the Triconex safety instrumented system controllers.
Learning: The response to Triton involved a coordinated effort by cybersecurity experts and industrial control system (ICS) professionals. The affected plant had to temporarily shut down its operations to investigate and remediate the issue. Mitigation efforts included system restoration, patching vulnerabilities, and enhancing cybersecurity protocols for the safety system.
2. Colonial Pipeline Ransomware Attack (2021):
Date: In May 2021, the Colonial Pipeline, a major fuel pipeline in the United States, fell victim to a ransomware attack.
Cause: The attack exploited a known vulnerability in the company’s virtual private network (VPN) and targeted the IT systems rather than the industrial control systems. The ransomware, DarkSide, encrypted critical data, leading to a temporary shutdown of the pipeline.
Learning: Colonial Pipeline opted to pay the ransom to expedite the recovery process, highlighting the delicate balance between paying cybercriminals and ensuring the continuity of critical services. Subsequently, the incident prompted increased scrutiny of cybersecurity practices in the energy sector and discussions on the ethics of ransom payments.
3. Oldsmar Water Treatment Facility Attack (2021):
Date: In February 2021, the Oldsmar water treatment facility in Florida experienced a cyber attack.
Cause: An unauthorized individual gained remote access to the facility’s supervisory control and data acquisition (SCADA) system and attempted to manipulate the levels of sodium hydroxide in the water supply to dangerous levels.
Learning: The quick response of a plant operator who noticed the unauthorized activity prevented any harm. The incident underscored the importance of multi-factor authentication and vigilant monitoring in critical infrastructure facilities. It also led to increased awareness of the potential vulnerabilities in water treatment systems.
4. SolarWinds Supply Chain Attack (2020):
Date: The SolarWinds supply chain attack was discovered in December 2020.
Cause: This sophisticated attack targeted SolarWinds, a software vendor widely used by government agencies and corporations. Malicious actors compromised SolarWinds’ software update mechanism, allowing them to distribute a trojanized version of the Orion software.
Learning: Mitigating the SolarWinds attack required a comprehensive response from affected organizations, involving the identification and removal of compromised software, security patching, and the implementation of enhanced supply chain security measures. The incident highlighted the importance of securing software supply chains against cyber threats.
5. Ukraine Power Grid Cyber Attacks (2015-2016):
Dates: In December 2015 and December 2016, Ukraine’s power grid suffered two separate cyber attacks.
Causes: The attacks, attributed to Russian state-sponsored actors, resulted in power outages affecting thousands of people. The adversaries employed malware to manipulate industrial control systems, causing disruptions in electricity distribution.
Learning: The incidents prompted increased cybersecurity measures in the energy sector, emphasizing the need for robust defense strategies and the importance of international cooperation in addressing cyber threats to critical infrastructure.
6. Stuxnet Worm (2010):
Date: Stuxnet, a highly sophisticated worm, was discovered in 2010.
Cause: Widely believed to be a joint effort by the United States and Israel, Stuxnet targeted Iran’s nuclear facilities. It exploited zero-day vulnerabilities in Windows operating systems and Siemens supervisory control and data acquisition (SCADA) systems to manipulate centrifuges used in uranium enrichment.
Learning: Stuxnet demonstrated the potential for cyber attacks to impact physical infrastructure. Its discovery prompted increased awareness of the need for robust cybersecurity measures in industrial environments and heightened international discussions on cyber warfare.
7. Dragonfly Campaign (2011-2014):
Dates: The Dragonfly campaign, discovered between 2011 and 2014, targeted energy sector organizations in the United States and Europe.
Causes: Attributed to state-sponsored actors, the campaign aimed to gather intelligence and potentially gain control over industrial control systems. It involved phishing attacks and the deployment of malware to compromise targeted networks.
Learning: The Dragonfly campaign highlighted the importance of threat intelligence sharing and collaborative efforts among government agencies and private sector organizations to defend against sophisticated cyber threats in the energy sector.
8. NotPetya Ransomware Attack (2017):
Date: The NotPetya ransomware attack occurred in June 2017.
Cause: NotPetya initially targeted Ukraine but quickly spread globally, affecting organizations across various sectors. It exploited vulnerabilities in software and used a compromised accounting software update to propagate.
Learning: The incident underscored the potential for ransomware to cause widespread disruption. Mitigation efforts involved the development of security patches, improved incident response strategies, and increased awareness of the need for regular software updates and backups.
9. Maroochy Shire Sewage Spill (2000):
Date: In 2000, the Maroochy Shire sewage spill incident occurred in Australia.
Cause: A disgruntled former employee gained unauthorized access to the sewage control system and released millions of liters of raw sewage into waterways, causing environmental damage.
Learning: The incident highlighted the insider threat and the importance of access control measures. It led to increased awareness of the need for comprehensive security protocols, employee training, and incident response plans in critical infrastructure facilities.
10. FireEye Red Team Tools Compromise (2020):
Date: In December 2020, cybersecurity firm FireEye discovered that its Red Team tools had been compromised.
Cause: The breach involved a sophisticated threat actor gaining access to FireEye’s internal systems and stealing its offensive cybersecurity tools, including those used for penetration testing.
Learning: FireEye’s response involved transparency about the breach, sharing details with the cybersecurity community, and developing and releasing countermeasures to mitigate the potential impact of the stolen tools.
Conclusion:
These ten industrial cyber attacks provide a comprehensive view of the evolving threat landscape facing critical infrastructure. Mitigating the impact of such incidents requires a combination of proactive security measures, rapid incident response, and ongoing efforts to enhance the resilience of industrial control systems. Organizations must remain vigilant, adhere to cybersecurity standards, and continuously update and test their security measures to safeguard against the ever-present and evolving cyber threats to industrial environments. The deep dive into these incidents serves as a valuable lesson, emphasizing the importance of a holistic and collaborative approach to industrial cybersecurity.